Searching the web it seems most people use “org.postgresql.ssl.NonValidatingFactory” to connect to Postgres from SQL Developer.
This doesn’t seem to be a good idea as the documentation states it is not secure:
Provide a SSLSocketFactory that allows SSL connections to be made without validating the server's certificate. This is more convenient for some applications, but is less secure as it allows "man in the middle" attacks.
Looking into the jar file under “/org/postgres/ssl” you’ll also find SingleCertValidatingFactory. Now that’s much better:
Provides a SSLSocketFactory that authenticates the remote server against an explicit pre-shared SSL certificate. This is more secure than using the NonValidatingFactory as it prevents "man in the middle" attacks. It is also more secure than relying on a central CA signing your server's certificate as it pins the server's certificate.
Let’s get to it…
The boring part: load the Postgres JDBC driver
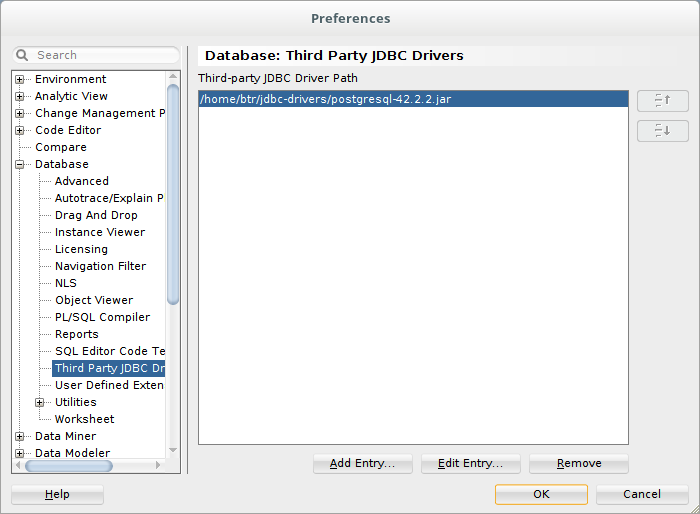
Go to “Tools” -> “Preferences…” -> “Third Party JDBC Drivers” and add the jar file
The tricky part: getting the connect string right (it’s actually not that hard)
Syntax:
<hostname>/<database>?ssl=true&sslfactory=org.postgresql.ssl.SingleCertValidatingFactory&sslfactoryarg=file:<path-to-cert-file>&
For example:
abc.xzy.us-east-1.rds.amazonaws.com/postgres?ssl=true&sslfactory=org.postgresql.ssl.SingleCertValidatingFactory&sslfactoryarg=file:/home/btr/certs/amazon-rds.crt&
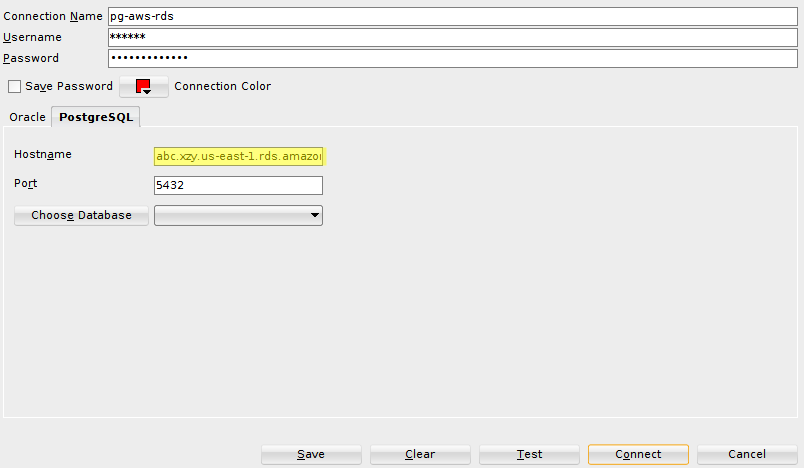
Enter this entire string in the “Hostname” field.
The exciting part: playing with your newly connected Postgres database 🙂
Keep it secure!
This worked perfectly — thank you!
Absolutely worked!